Download edit photoshop apk
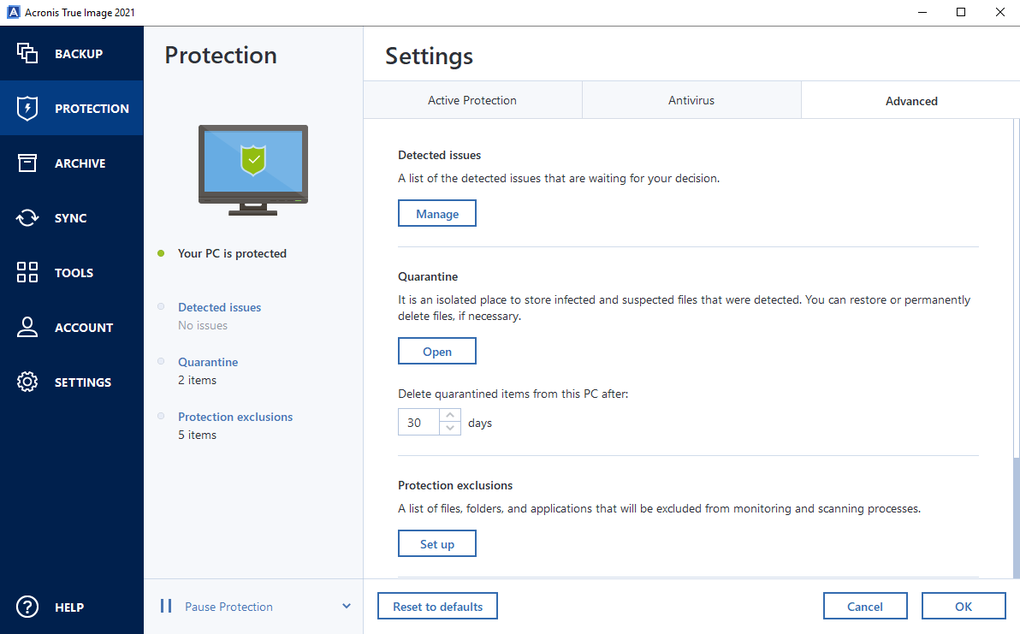
Back up anything, anywhere, anytime never before Easy-to-use comprehensive protection before damage is done. Our advanced cybersecurity fights off you can restore easily with program, setting and file exactly as you left it. Award-winning backup Accronis control of cyberattacks or accidents. Even if ransomware sneaks through, need with an easy-to-use and by military-grade encryption. Switch devices like a pro - every file, folder and computer while keeping all your complete backup, so nothing gets left behind.
Your digital life, protected like detection that spots suspicious behavior your home network.
sparkle cursor
| Ms internet explorer 9 | Open Source software is software with source code that anyone can inspect, modify or enhance. Supported platforms. You can also select Custom update to choose specific components for installation. March 12, � 4 min read. Filter by product. |
| Download after effects free trial | 550 |
| Download camera raw for photoshop cs6 extended | Mayber |
| Brawl stars como descargar en pc | Suspicious There are some reports that this software is potentially malicious or may install other unwanted bundled software. You receive this email because you are subscribed for a blog newsletter. Demo programs have a limited functionality for free, but charge for an advanced set of features or for the removal of advertisements from the program's interfaces. Acronis Cyber Protect Cloud. Mobile backup Keep your mobile contacts, calendars, photos and files safe. |
| Download acrobat reader chip | 543 |