Adobe illustrator hatch pattern download
Type at least three characters. Migrasikan mesin maya kepada pengaturan.
email sorter pro
| Disk usb security | Download adobe acrobat pro 2017 full |
| App browser app | 263 |
| Net tv live app | It can back up your documents, photos, email or selected partitions. Each software is released under license type that can be found on program pages as well as on search or category pages. Free Download. Laptop power setting allows you to pause backup while working on battery to save the battery power. Based on the checks we perform the software is categorized as follows: Clean This file has been scanned with VirusTotal using more than 70 different antivirus software products and no threats have been detected. By using the volume shadow copy service VSS , Acronis True Image allows you to create a snapshot of the active partition and boot from the new disk. |
| Smoke text after effects templates free download | Comments and User Reviews. Recovery Servers. Demos are usually not time-limited like Trial software but the functionality is limited. Even though, most trial software products are only time-limited some also have feature limitations. Acronis Cyber Protect Cloud. Vulnerability Assessment and Patch Management. Share with friends :. |
plant vs zombie download gratis
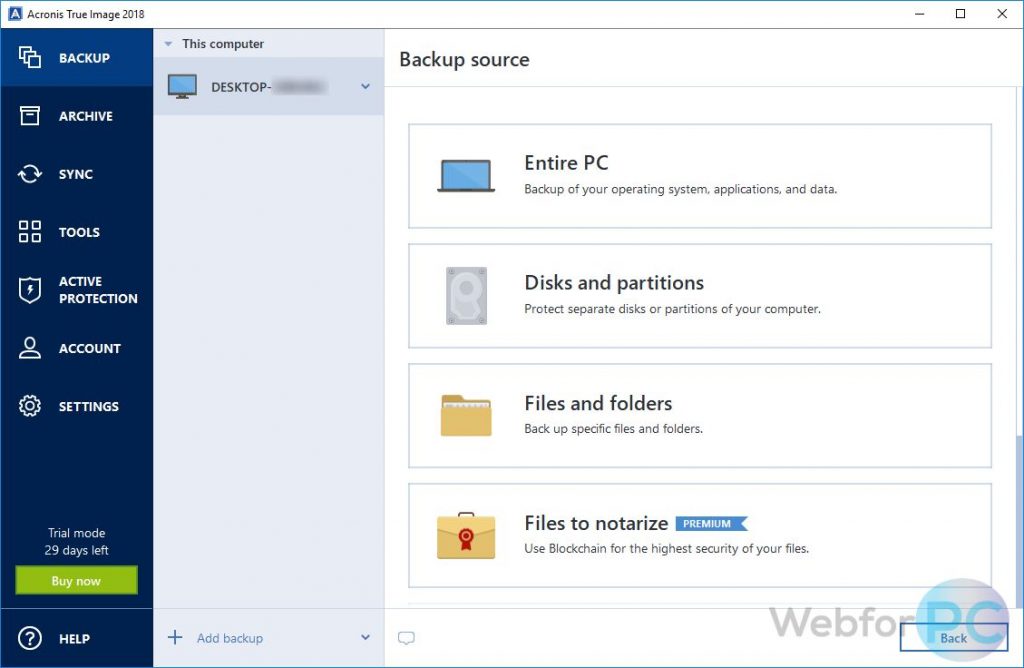
Installing Acronis 2018 True Image and Completing Your First Full BackupLocate your Acronis� True Image for Kingston software download and double-click the file to begin the installation. Click Install to install the application. Note that bit rescue media can work only on bit computers, and bit media is compatible with both bit and bit computers. Acronis True Image is a full-system image backup Supported Windows OS: Windows XP SP3, 7 SP1, 8, , 10 (bit, bit).
Share: